Why Malware Is Far More Malicious Than You Know
Learn why malware that is lurking behind every corner is far more nefarious than you may be aware of.
This article is more than 2 years old

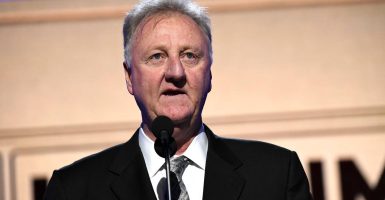
Tracking and surveillance are at a whole new level in 2022. As technology advances, hackers adapt with it, finding unique ways to manipulate and infiltrate people’s personal data. For many who carry around a smartphone, the possibility for someone to pick up their location or hack into their system through malware is an ever-growing threat. Though you might suspect that powering a phone down would shut off those possibilities, hackers could still find your location through a turned-off smartphone.
With the latest update for Mac iOS systems, people can still track your location if your phone has been shut down. Specific wireless chips inside the phone still send out signals when the phone is off, keeping its location intact. Because of these chips, a study performed by a group of researchers in Germany found that hackers could potentially break into a specific chip and install malware.
Researchers at the Technical University of Darmstadt in Germany found a particular pesky chip in iPhones that could create real damage to a user. One chip that enables Bluetooth can be infiltrated and have malware installed on it, even when the phone has been shut off. These researchers concluded that it’s possible for someone to install nefarious programs on a shut-off phone through the Bluetooth chip, though there’s no concrete evidence this type of attack can or will happen. The paper published was only about the hazardous possibilities of these chips that continuously send out signals even when the phone is not operating.
This group of researchers did find a potential defense mechanism in these phones that would make it hard for hackers to install malware. Hackers would have to jailbreak an iPhone to access the Bluetooth chip, which is relatively difficult to do. But if a hacker can access the Bluetooth chip, they’d have a more significant entry into that user’s data. It’s a beneficial chip to access for hackers since one can acquire data through it while the phone is off.
These wireless chips that consistently send out signals run something called NFC or Near Field Communication. iPhone apps like Apple Pay and the Bluetooth app use NFCs, outputting wireless signals even when the phone is dormant. These systems are also in place for Find My iPhone apps that help locate a phone when it’s not operable. Though this is extremely helpful for finding lost items, it could potentially lead to a hacker putting malware on your device if they successfully infiltrate your phone.
Though one could hack into the Bluetooth app and install malware, researchers noted that Bluetooth chip access doesn’t mean a hacker could get into the whole iPhone. Installing a virus into the Bluetooth chip could be helpful as an addition to already implanted malware, but wouldn’t operate adequately as a stand-alone virus. The researchers also didn’t conclude if someone could hack into the Bluetooth chip and successfully jump into the phone’s central database. Having a smartphone on your person is an everyday occurrence in modern society, but it could lead to a high-risk situation if a hacker puts malware on your dormant iPhone.