Intel Is Hacking Its Own Computer Chips?
Find out why Intel thinks hacking its own computer chips is a good idea.
This article is more than 2 years old
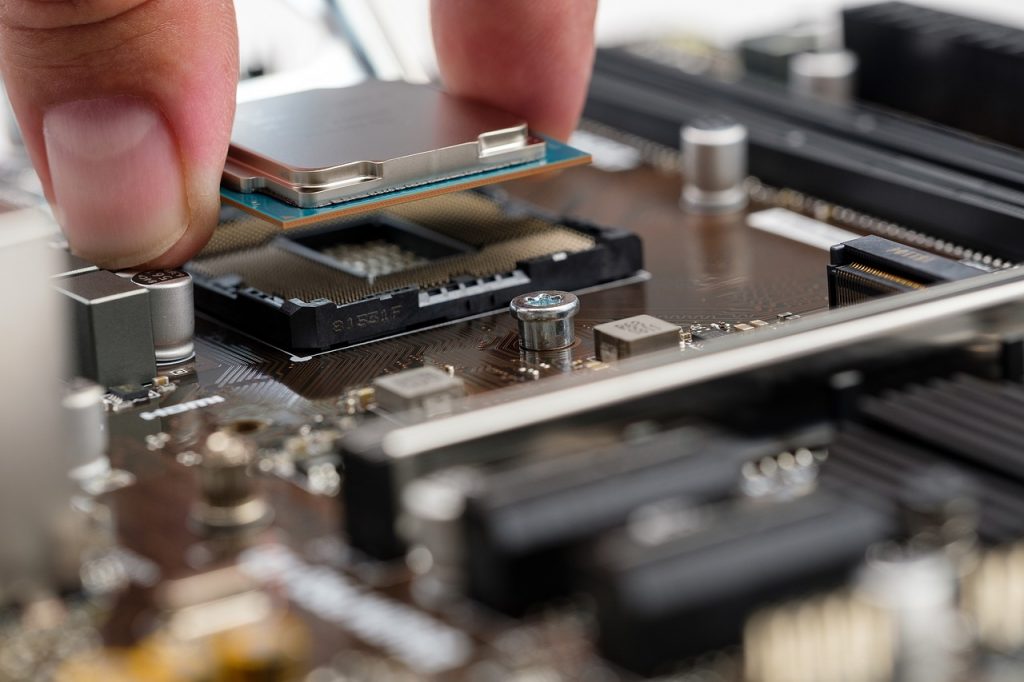
Intel, the tech company known for producing processors and hard drives, has a peculiar way to investigate its computer chips. The company’s employees are taught to hack into their own chips, guaranteeing they can find flaws in the software before hitting the market. After Intel created a hacking group as part of their corporation, the employees continued to investigate chips to understand their deficiencies better.
Intel’s highly intelligent hacking group, Intel Security Threat Analysis and Reverse Engineering, was created five years ago to deal with the rise in malicious activity. Since its inception, the group has been comprised of 20 researchers who work in specially-constructed labs for their hacking pursuits. The researchers take time examining chips before they get released to the public, ensuring that they have no weak spots for potential invasions.
Intel is taking a proactive approach to defending its consumers from malicious hackers. One of the most common tactics that hackers use is to figure out mistakes in software coding, identifying code inconsistencies to sneak their ways in. Another way to get into a laptop‘s data is a physical action, like playing with the computer’s motherboard. The iStare researchers combat tangible and virtual ways hackers could steal data by implementing all kinds of precautions.
Researchers working for Intel apply different circuit boards, strategic electromagnetic pulses, or change heat emissions that accidentally release data. An electronic, magnetic pulse, or EMP, can be utilized to scramble certain software protections. Intel’s researchers are doing everything they can to prevent an EMP ambush, an extremely new and advanced way to hack.

iSTARE’s group manager, Uri Bear, reported on the intense nature of the employee’s mission. “We basically emulate the hacker,” Bear stated, explaining their investigative procedures. Intel workers within the group have to think like hackers and anticipate possible attacks. After figuring out malware in computer chips, they also have to conjure up future scenarios and install additional prevention software.
Uri Bear also included some interesting, more benevolent words regarding devious hackers. Bear commented on life without hackers stating, “everything would be stale.” Though these intruders bring stress and threaten security for many, Intel workers are pushed to make better technology when investigating their own chips. Spending time crafting unhackable technology makes their skills and inventions even more developed.
iSTARE gets its name from its significant investment in reverse engineering. The staff of Intel’s premier anti-hacking group is tasked with working backwards, starting with a finished chip and examining its production in reverse. The researchers start with an electron microscope, investigating a chip’s minuscule programming systems. After researching a design thoroughly, iSTARE then acts as a consulting group, providing recommendations to Intel on what to do with a flawed computer chip.
iSTARE, as a successful Intel researching group, often has more duties than they can handle. Since the staff is only 20 individuals, they usually don’t have the time or resources to investigate every request. This means that the presidents of Intel’s security research team make executive decisions regarding chip investigations, utilizing generalized findings to analyze malware without physical examinations.