Airports Using Controversial Technology To Confirm Travelers’ Identities
Travelers will now be subject to one type of controversial technology already in use at Airports.
This article is more than 2 years old

When looking at various types of biometric technology, some airports have chosen facial recognition scanning over fingerprints, iris scans, and other biometric technologies. Why? Because it is such a simple process. Travelers introduce themselves and their belongings, then pose for a brief photo. Based on a chat with the traveler about the purpose of the trip, the officer has the knowledge they need to determine whether further scrutiny is required. It’s comforting to know that businesses can take advantage of technology that is more capable of making comparisons. More so, new tech allows the officer to retain ultimate decision-making authority and gives travelers the option of opting out.
Another reason facial recognition biometrics is helpful is that it follows a simple procedure and assists officers in establishing travel intent more quickly. It also does a better job of spotting potential impostors. The third reason comes in the form of additional health benefits by improving security at a time and location where people are already required to show themselves for identity verification. Furthermore, the tech can be used to provide touchless travel, which is essential for restricting pathogen spread.
There have been roughly 300 impostors identified utilizing the facial recognition technology since the deployment of the new facial recognition tech. The tech was first used in airports for identification purposes about three years ago. These imposters predominantly used the tech in the air passenger environment and to a lesser extent in marine.
Businesses that can most benefit from facial recognition tech are those that entail identifying people at a time and place when they would ordinarily expect to be asked to verify their identification. There is no gathering photographs from the internet or trawling social media to perform verification. Instead, galleries consisting of photos from the US Library of Congress are used to perform verify identity. When establishing a gallery, that photo isn’t linked to any data and can’t be reverse-engineered. This is necessary to ensure the data and photos cannot be compromised. The average retention time for images in the United States is less than 12 hours, and typically much less.
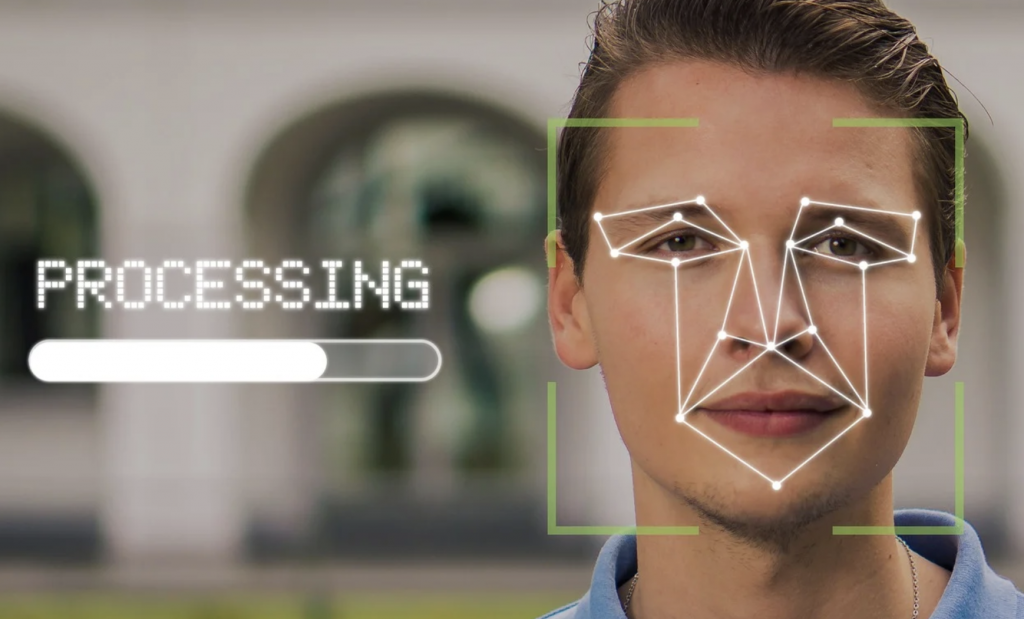
Signage is put up at all of the ports of entry to let travelers know they can opt-out of the facial recognition technology. Individuals who choose to opt-out must inform the officer at the time of inspection. Scrutiny from privacy advocates has helped make the tech more defined and safe to use. There are a lot of misconceptions and misinformation out there about tech and surveillance. There are always real concerns whenever new technology is introduced, and any tech company will do well to welcome issues and concerns and address them accordingly.
In addition to airports, there are many ways to make use of facial recognition technology. Facial recognition technology works by scanning and measuring specific areas of a person’s face. Even if two persons appear to be identical, there are tiny variances that we may not notice in person. These nuances can be detected using facial recognition technologies. The facial recognition technology examines a person’s face for information such as dimensions of the eye sockets, length of the jaw, breadth of the nose, and the distance between the brow and the chin. Thanks to advancements in tech, facial recognition technology has improved to the point that it is now more accurate than ever and has the ability to detect up to 80 distinct facial characteristics.